Zero-day exploits are one of the most dangerous threats in today’s digital world. They can cause serious harm to businesses, government organizations, and individuals alike. But what exactly is a zero-day attack, and how can you prevent it? In this blog, we’ll break down the concept of zero-day attack prevention and provide you with simple steps to protect your systems.
What Is a Zero-Day Attack?
Imagine this: You’ve just bought a brand-new phone, and you’re excited to use it. You turn it on, connect it to the internet, and start downloading your favorite apps. But then—bam! Something goes wrong. A hacker takes control of your phone without you even knowing it.
A zero-day attack works in a similar way. It’s a type of cyberattack that happens when hackers take advantage of a security vulnerability in software or hardware that the creators don’t yet know about. This means the attackers can strike before anyone even realizes there’s a hole in the system. Zero-day exploits are especially dangerous because there’s no time to patch the vulnerability before it’s used against you.
Think of it like a thief finding an unlocked door. While the door is open, the thief can sneak in without being noticed.
Why Are Zero-Day Attacks So Dangerous?

Zero-day attacks are dangerous for several reasons:
- No Defense: There is no warning. The vulnerability hasn’t been discovered yet, so antivirus programs and firewalls can’t stop the attack.
- High Impact: These attacks can steal data, damage systems, or cause a network to crash.
- Hard to Detect: Since there’s no signature of the attack yet, it can be challenging to find out that you’re under threat.
It’s like walking into a dark room where someone is hiding. You don’t even know they’re there until it’s too late.
How Do Zero-Day Exploits Work?

To fully understand how to prevent zero-day attacks, let’s take a deeper look at how they happen.
- Discovery of a Vulnerability: A hacker discovers a flaw or bug in a piece of software or hardware. This flaw is usually invisible to the developer and anyone using the system.
- Creating the Exploit: Once the hacker knows about the vulnerability, they create an exploit—a program or piece of code designed to take advantage of this flaw.
- Launching the Attack: The hacker then launches the attack on a system or network, using the exploit. Since no one knows about the flaw, there is no fix in place to stop it.
In many cases, zero-day attacks happen before developers can fix the vulnerability with a software update. This gives the hackers a big advantage. It’s like a burglar discovering a weak spot in your front door before you even know it’s there.
How to Prevent Zero-Day Attacks?
The good news? Zero-day attack prevention is possible. While no method can guarantee 100% protection, there are several steps you can take to reduce the risk of being a victim. Let’s dive into some practical, easy-to-understand strategies.
Keep Your Software Updated
This one might seem obvious, but it’s also the most important.
Software developers are constantly working to fix bugs and vulnerabilities. When they find an issue, they release security patches to fix it. If you don’t install these updates, you leave your system exposed.
- Why it works: Regular updates patch known vulnerabilities and make it harder for hackers to exploit them.
- How to do it: Set your software and operating systems to automatically update, so you never miss a critical fix.
Remember: Think of updates as locking the doors of your house every night. If you leave them unlocked, anyone can sneak in.
Use a Multi-Layered Security Approach
One layer of security isn’t enough. You need multiple layers, or defense-in-depth, to protect your system.
- Firewalls: These act as barriers between your network and the outside world, blocking malicious traffic.
- Antivirus and Anti-Malware Tools: These tools help detect suspicious behavior and known threats. While they can’t stop zero-day attacks directly, they may catch some signs of the exploit in action.
- Intrusion Detection Systems (IDS): These systems monitor your network for unusual activities. If a hacker tries to exploit a vulnerability, an IDS can alert you.
A multi-layered defense is like locking the door, installing an alarm system, and keeping a watchdog on the lookout for trouble.
Implement Zero Trust Security
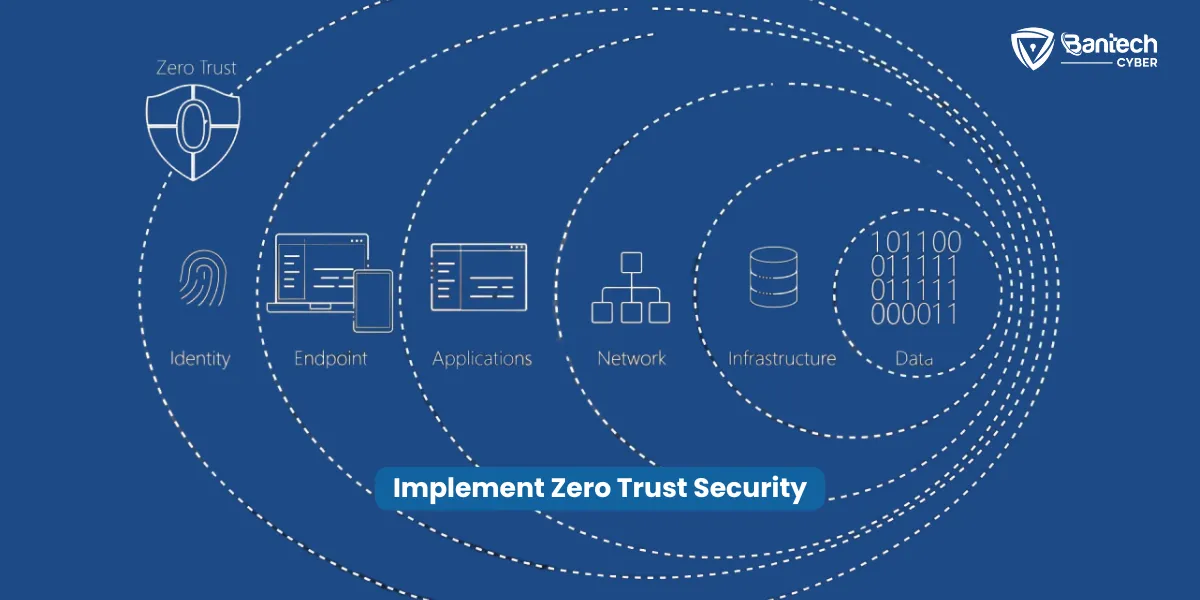
Zero Trust is a security model based on the idea that no one is trusted by default, whether they are inside or outside your network.
- How it works: Every user, device, or application that tries to access your system must be verified and authenticated.
- Why it helps: Even if an attacker finds a vulnerability, they won’t be able to move freely inside your network because they must prove their identity at each step.
It’s like having a bouncer at every door, checking the ID of everyone who tries to enter.
Monitor Your Network and Systems Regularly
The sooner you notice something strange, the better. Continuous monitoring can help you detect potential zero-day exploit attacks before they cause significant damage.
- How it works: Set up systems to alert you whenever there’s unusual behavior on your network.
- Why it helps: Detecting an attack early gives you time to respond and contain the damage.
This is like checking your home security cameras regularly to spot any suspicious activity before it escalates.
Educate Employees and Users
Human error is often the weakest link in cybersecurity. Hackers use methods like phishing to trick employees into downloading malicious files or clicking on harmful links.
- How it works: Provide training on how to recognize phishing emails and suspicious links. Make sure everyone knows the risks of opening unknown attachments or visiting unsafe websites.
- Why it helps: Well-trained employees can stop attacks before they start.
It’s like teaching your kids to lock the doors and windows when they leave the house.
Use Application Sandboxing
Sandboxing is a technique that isolates programs to prevent them from causing harm to your system.
- How it works: If a user or attacker tries to run malicious software, the sandbox isolates it from the rest of your network, preventing it from doing damage.
- Why it helps: If a zero-day exploit is launched, it can be contained within the sandbox without harming your network.
It’s like putting a potentially dangerous item in a secure box, where it can’t hurt anything.
Backup Your Data Regularly
In case an attack does slip through, data backups are a lifesaver.
- How it works: Regular backups ensure that you can restore your systems to a safe state if data is lost or corrupted during an attack.
- Why it helps: If your system is compromised, you can quickly recover without significant data loss.
Think of backups like having spare keys to your house. If the original gets lost or stolen, you still have access.
Conclusion: Preventing Zero-Day Attacks is Possible
Zero-day attack prevention isn’t easy, but with the right steps in place, it’s absolutely achievable. By keeping your software updated, using a multi-layered security approach, monitoring your systems, and training your employees, you can protect your business from these dangerous threats.
At Bantech Cyber, we specialize in helping businesses and governments stay secure. Our team of cybersecurity professionals can guide you through the process of setting up and maintaining the strongest defenses against zero-day attacks.
Remember: While no one can predict the next attack, you can always be ready to defend against it. With the right preparation and a little effort, your organization can stay one step ahead of the hackers.
Key Takeaways:
- Keep your software up-to-date.
- Use multi-layered security for maximum protection.
- Educate employees to spot potential threats.
- Regularly back up your data.
By following these simple steps, you’ll significantly reduce your chances of falling victim to a zero-day exploit attack. Stay proactive, stay protected!
