Imagine this: hackers use automated bots to try thousands of stolen usernames and passwords to break into accounts. This is called credential stuffing. It’s a sneaky attack that can cause a lot of damage. If you don’t stop it, it can lead to lost personal information or even hacked accounts.
In this blog, we’ll explain what credential stuffing is, why it’s dangerous, and how to prevent credential stuffing attacks. We’ll also give you simple steps you can take to keep your accounts safe.
Simply put, to prevent credential stuffing, you should —
- use strong, unique passwords,
- enable multi-factor authentication,
- and monitor for unusual login activity.
Read to learn in detail.
Key Takeaways:
|
What is Credential Stuffing?
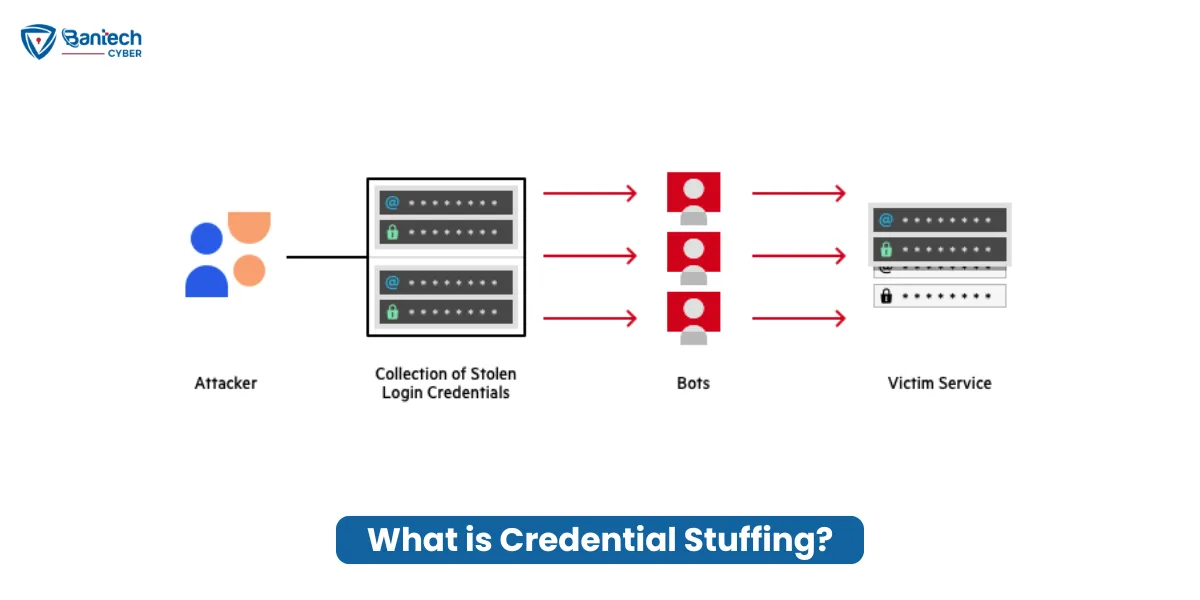
Credential stuffing is when cybercriminals use automated bots to try stolen usernames and passwords to break into accounts. These bots try many combinations quickly, hoping to find the right one. It’s like a thief trying to unlock a door with thousands of keys until one fits.
How It Works
The hackers get large lists of usernames and passwords. These lists often come from previous data breaches, where companies’ data has been leaked. They then use bots to try these combinations on other websites.
Since many people use the same username and password on multiple sites, these attacks can work well.
Difference Between Credential Stuffing and Other Cyber-Attacks
- Phishing: This is when attackers trick you into giving them your information (like clicking on fake links or opening harmful emails).
- Credential Stuffing: This attack doesn’t need to trick you. It simply uses stolen login details to break into your accounts automatically.
Why Credential Stuffing is Dangerous
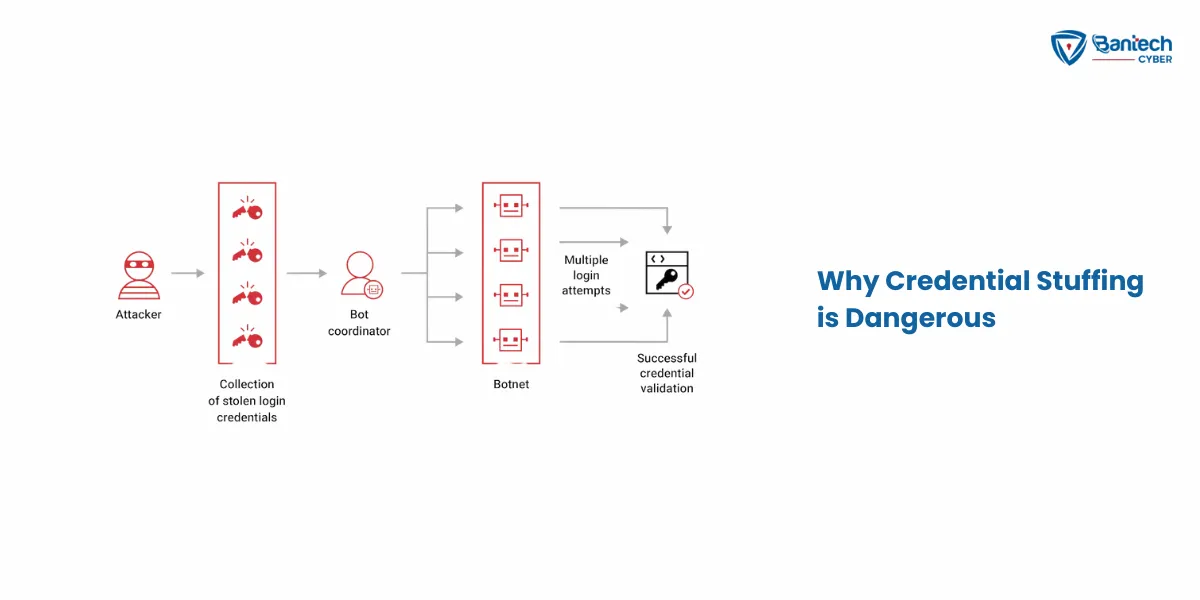
Potential Consequences
- Data Breaches: If hackers get into your accounts, they can steal personal information, like your name, address, or payment details.
- Unauthorized Access: Hackers can gain access to everything in your accounts, like emails, social media, or banking apps.
- Loss of Sensitive Information: If your data is stolen, it can be used for identity theft or sold on the dark web.
Impact on Businesses and Users
- For Businesses: Credential stuffing can damage your reputation, cause financial loss, and hurt customer trust.
- For Users: Personal accounts, social media profiles, and bank accounts can be hacked, causing financial and emotional stress.
Common Vulnerabilities That Enable Credential Stuffing
- Weak Password Policies
- Weak passwords are easy for bots to guess. Simple passwords like “12345” or “password” can be cracked quickly.
- Reused Passwords Across Multiple Accounts
- Many people use the same password for different accounts. If one account gets hacked, the hacker can try the same login on other accounts.
- Poor Account Security Measures
- Not using tools like multi-factor authentication (MFA) or not having alerts for suspicious activities makes it easier for hackers to gain access.
At Bantech Cyber, we provide strong cybersecurity to keep your business safe. Our Managed Cyber Security Services will surely protect your business with 24/7 monitoring, fast threat detection, and proactive security.
We help secure your systems and data from cyber threats like Credential Stuffing Attacks.
How to Prevent Credential Stuffing Attacks
Here are easy ways to do credential-stuffing attack prevention.
1. Use Strong, Unique Passwords

A strong password is long, random, and includes a mix of letters, numbers, and symbols.
- Do: Use passwords like “M$7dL@23gNf!9”
- Don’t: Use passwords like “password123” or “qwerty”
Using unique passwords for every account is also important. Don’t use the same password on more than one site. Yes, it’s extra work, but it keeps you safe.
2. Implement Multi-Factor Authentication (MFA)

MFA adds an extra layer of security. Even if a hacker gets your password, they can’t log in without another factor.
Types of MFA:
- SMS-based: You get a code on your phone.
- Authenticator Apps: Use apps like Google Authenticator or Authy for time-based codes.
- Biometrics: Fingerprint or face recognition.
3. Monitor for Unusual Login Activity

Set up alerts to notify you if someone logs in from an unusual location or device. For example, if you normally log in from your phone in one city and suddenly someone logs in from a different country, you’ll know something’s wrong.
4. Use CAPTCHA to Prevent Automated Attacks

CAPTCHA is a test that asks you to prove you’re human (like clicking all the pictures with traffic lights). This blocks bots from trying passwords too quickly.
Types of CAPTCHA:
- Image recognition: Pick all the pictures with traffic lights.
- reCAPTCHA: Google’s version asks you to click a box saying, “I’m not a robot.”
5. Rate Limiting and Account Lockouts
Rate limiting controls how many times a person can try to log in within a certain time. If someone tries too many times and fails, their account should be locked for a while.
This slows down bots and prevents them from trying thousands of passwords in minutes.
6. Encourage Password Managers

Password managers help you store unique and strong passwords for all your accounts. Instead of trying to remember each password, the manager does it for you.
Benefits:
- Safe storage of passwords
- Automatically generates strong passwords
- Avoids password reuse
7. Regularly Update and Patch Systems

Always update your software and security systems to stay protected. Hackers often exploit old, unpatched vulnerabilities. Regular updates keep your accounts and systems protected.
In addition, you can check out these blogs for simple guides on stopping Malware Attacks, XSS Attacks, SQL Injection Attacks, and Zero-Day Exploits!
Best Practices for Organizations

If you run a business, make sure you:
- Conduct Regular Security Audits: Regularly check your security measures.
- Educate Employees and Customers: Teach them about strong passwords and MFA.
- Collaborate with Cybersecurity Experts: Experts can help you stay ahead of attackers.
Tools and Technologies to Prevent Credential Stuffing
Here are some tools that can help prevent credential stuffing:
- Bot Detection Software: Blocks bots before they can even start attacking.
- Web Application Firewalls (WAF): Filters bad traffic and blocks harmful requests.
- Credential Stuffing Protection Tools: Tools that specifically look for credential stuffing attempts.
Selecting the right tool depends on your business needs and the level of security you need.
Also, you can read these helpful blogs to understand how to prevent cyber attacks, ransomware, DDoS attacks, and Man-in-the-Middle Attacks!
Wrapping Up
So, coming to this point, we can assume that you now have a pretty good idea of how to prevent credential stuffing. Credential stuffing is a real threat, but you can take the above steps to protect yourself and your business.
Use strong passwords, enable MFA, watch for unusual activity, and keep your systems updated. By following these easy tips, you can stop hackers in their tracks and keep your information safe.
Remember, being proactive about security is the best way to avoid these attacks.
Don’t wait until it’s too late!
