Cybersecurity is super important these days. One of the sneakiest threats out there is a Man-in-the-Middle (MITM) attack. In this type of attack, hackers secretly spy on or steal sensitive data, like passwords or financial information.
But don’t worry! By the end of this blog, you’ll know what MITM attacks are, how they work, and how to prevent Man-in-the-Middle attacks.
Here’s the brief for you: to prevent MitM attack—-
- use strong passwords,
- enable two-factor authentication,
- avoid public Wi-Fi,
- check for HTTPS,
- and use a VPN for secure browsing.
Let’s get into the details of this topic.
Key Takeaways:
|
Types of Man-in-the-Middle (MITM) Attacks
MITM attacks are sneaky. Hackers use different tricks to steal your data. Let’s go over the most common ones:
1. Wi-Fi Eavesdropping
Hackers create fake public Wi-Fi hotspots. These hotspots look free and safe to use. But when you connect, they can watch everything you do.
- They can see your passwords, emails, and credit card details.
- For example, if you log in to your bank account on their Wi-Fi, they can steal your login info.
2. Spoofing (ARP/DNS)
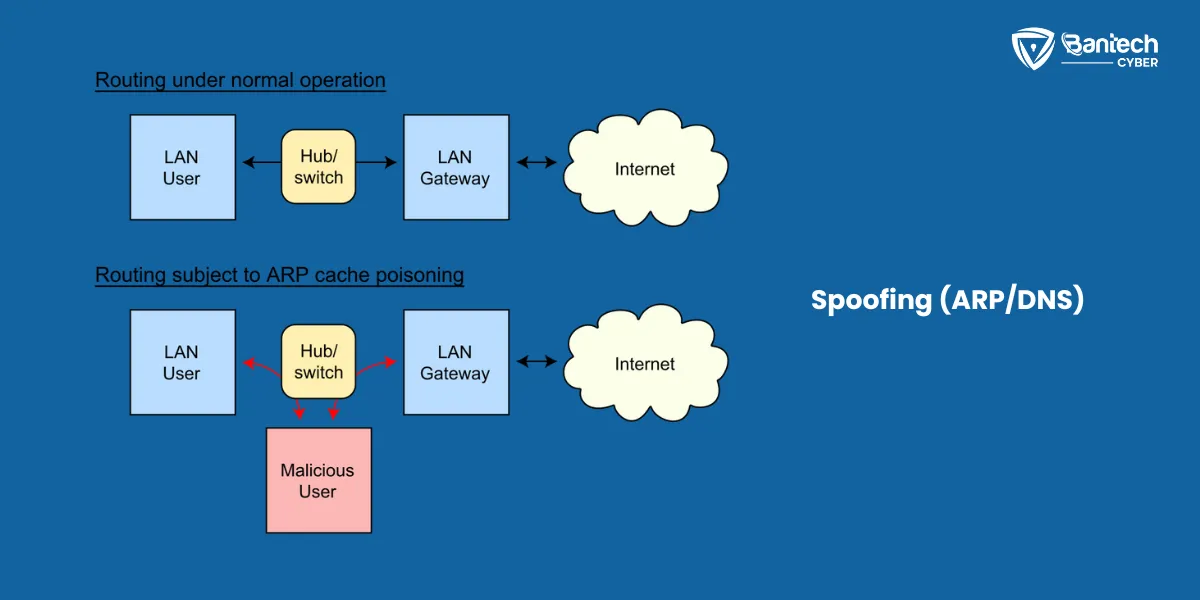
Hackers trick your device into sending data to them instead of a trusted server.
- ARP Spoofing targets your device’s connection to the local network.
- DNS Spoofing redirects you to fake websites that look real.
- For example, you may type “www.mybank.com,” but end up on a fake website that steals your password.
3. HTTPS Stripping
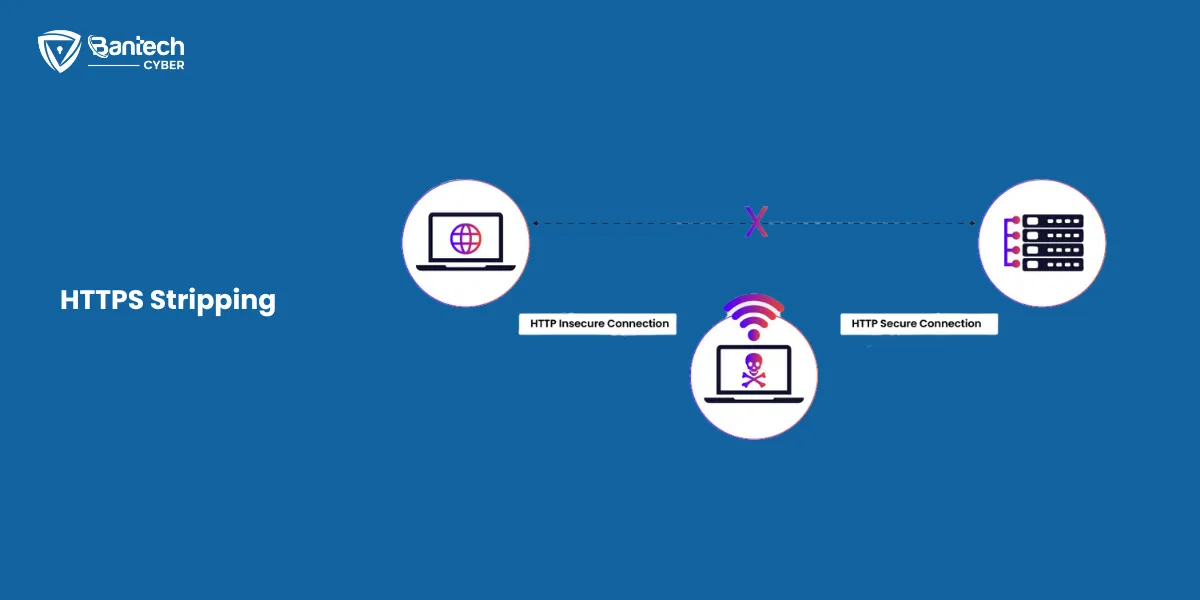
Hackers force your connection to switch from HTTPS (secure) to HTTP (not secure).
- HTTPS encrypts your data, but HTTP does not.
- They can then see everything you type on the website.
- For example, you might log in to a shopping website, but hackers will see your username and password in plain text.
How to avoid this: Always check for “https://” and the padlock symbol in your browser’s address bar.
4. Email Hijacking

Hackers break into email conversations.
- They pretend to be someone you trust, like your boss or a company.
- They might ask you to send money or share private information.
- For example, you could get an email pretending to be from your bank asking for your account details.
5. Session Hijacking
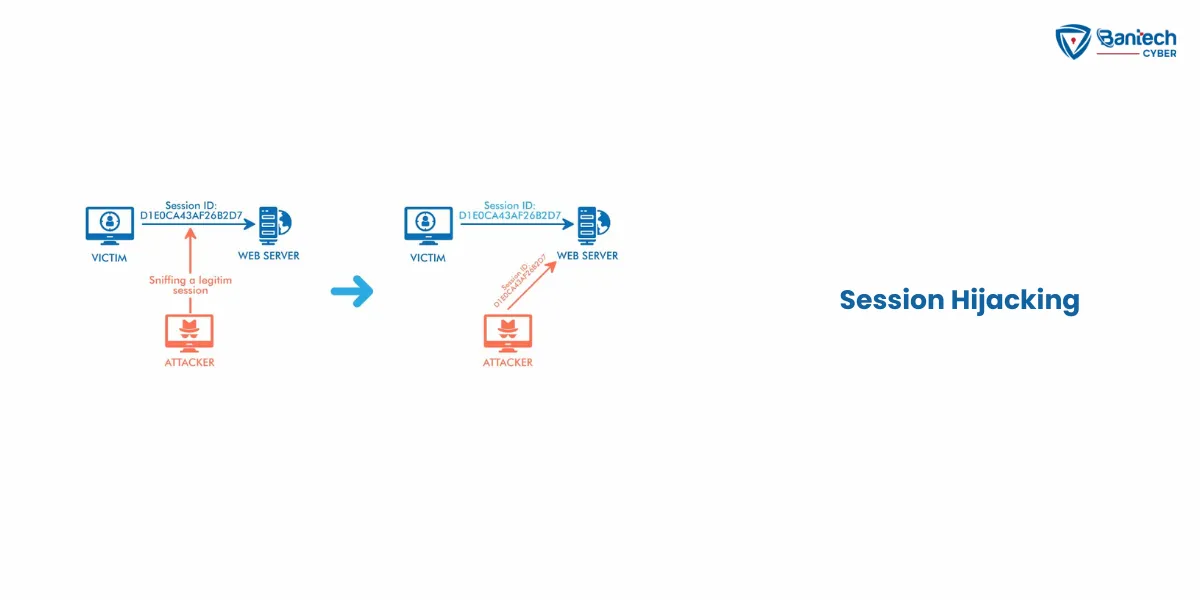
Hackers steal session tokens from websites you’ve logged into.
- Session tokens are small pieces of data that websites use to keep you logged in.
- Once hackers have the token, they can act as you.
- For example, they can log in to your social media account and send messages pretending to be you.
Other MITM Tricks to Watch Out For
- Fake Mobile Apps: Hackers create apps that look real but steal your data.
- Bluetooth Interception: Hackers can access your data through open Bluetooth connections.
- IoT Device Attacks: Devices like smart speakers or cameras can also be targeted.
How to Prevent Man-in-the-Middle (MITM) Attacks
Preventing MITM attacks doesn’t have to be hard. Let’s go over some easy tips to keep your data safe.
1. Use Secure Wi-Fi

Public Wi-Fi is risky. Hackers love to use it for attacks.
- Avoid public Wi-Fi whenever you can.
- If you must use it, connect through a VPN (Virtual Private Network). VPNs encrypt your data, making it harder for hackers to read.
- At home, make sure your Wi-Fi has a strong password. Don’t use something easy to guess, like “123456.”
2. Check HTTPS Before You Enter Info
Not all websites are safe.
- Always observe the address bar for “https://” before entering personal details. The “S” means it’s secure.
- Look for the little padlock symbol 🔒 in the browser.
- If you see a warning about an insecure website, don’t continue.
3. Enable Two-Factor Authentication (2FA)
2FA includes an extra layer of security to your accounts.
- After entering your password, you’ll need to verify yourself using something else, like a text code or an app.
- Even if hackers steal your password, they basically won’t be able to log in without the second step.
- Use 2FA on important accounts like banking, email, and social media.
4. Keep Devices and Apps Updated
Updates aren’t just for new features. They fix security holes, too.
- Always update your phone, laptop, and apps when new updates are available.
- Turn on automatic updates so you don’t forget.
- Outdated software is an easy target for hackers.
5. Avoid Suspicious Links and Attachments

Be careful about clicking on things online.
- Skip clicking on links or downloading attachments from unfamiliar senders.
- Always double-check the sender’s email address. Hackers can make emails look real but change small details in the address.
- If something feels off, don’t click it.
6. Use Strong, Unique Passwords
Weak passwords are simply like leaving your door unlocked.
- Use long/ unique passwords with a mix of letters, numbers, and symbols.
- Don’t reuse passwords for multiple accounts. If one gets hacked, they all do.
- Use a password manager to create and store passwords safely.
7. Install Security Software

Antivirus and firewalls are your friends.
- Install antivirus software on all your devices. It can detect and block threats.
- Keep your firewall turned on. It blocks unauthorized access to your network.
- Some security tools also warn you about unsafe websites.
8. Log Out of Accounts When Not in Use
Always log out, especially on shared or public devices.
- If you stay logged in, hackers can steal your session and pretend to be you.
- Use private browsing mode if you’re using a public or shared computer.
9. Disable Bluetooth and File Sharing
Hackers can sneak in through open connections.
- Turn off Bluetooth and file-sharing features when you’re not using them.
- Don’t accept random file transfers or pairing requests from unknown devices.
10. Be Wary of Fake Apps and Websites
Hackers create apps and websites that look real but are fake.
- Always download apps from trusted/ reliable sources like Google Play or the Apple App Store.
- Double-check the URL of a website before entering personal information.
11. Monitor Your Accounts Regularly

Keep an eye on your bank accounts, emails, and social media.
- Look for unusual activity, like messages you didn’t send or purchases you didn’t make.
- If you see anything strange, change your password immediately and report it.
Extra Tips for Businesses
- Use end-to-end encryption for communication tools.
- Train employees to spot phishing scams and suspicious activity.
- Set up a secure network with strong passwords and firewalls.
If you want to learn, read these blogs to get a clear guide on preventing cyber attacks, ransomware, and DDoS attacks!
Man-in-the-Middle Attack Techniques
Attackers use smart tricks to steal your information. Let’s look at some of their methods:
| Technique | How It Works |
| Packet Sniffing | Hackers capture unencrypted data sent over networks. |
| Man-in-the-Browser | Malware secretly modifies your browser activity. |
| SSL Hijacking | Hackers intercept your encrypted connection and replace it with their own. |
| Email Interception | Attackers hijack emails and send fake responses to fool victims. |
| Fake Wi-Fi Hotspots | Hackers create free hotspots to trick users into connecting. |
If you want to learn, read these blogs to get a clear guide on preventing Malware Attacks, Phishing Attacks, SQL Injection Attacks, and Zero-Day Exploits!
How to Detect a Man-in-the-Middle Attack
Spotting an MITM attack early can save you big time. Here are signs to watch for:
- Strange Login Requests: If a website suddenly asks for personal info, be cautious.
- Browser Warnings: Your browser might warn you about an insecure connection. Don’t ignore it!
- Unusual Pop-Ups: If you see pop-ups asking for sensitive details, stop and check the website’s authenticity.
- Slow or Lagging Connections: MITM attacks can slow your internet speed.
- Emails That Feel “Off”: If emails look weird or ask for sensitive info, verify them with the sender.
What to Do After a Man-in-the-Middle Attack: Quick Solutions
If a man-in-the-middle attack has already happened, act fast.
- Disconnect Immediately: Turn off Wi-Fi, Bluetooth, or any network connection. This stops more data from being stolen.
- Change Your Passwords: Use a safe device to update all your passwords. Make them strong and unique.
- Check for Unauthorized Activity: Look for strange logins, messages, or transactions on your accounts.
- Update Devices and Software: Install the latest updates on your devices to fix security holes.
- Enable Two-Factor Authentication (2FA): Add extra security to your accounts to stop hackers from getting in again.
- Contact Your Bank or Service Provider: If financial info is at risk, alert your bank right away. They can help secure your accounts.
- Use Antivirus Software: Run a full scan to remove any malware the attacker might have planted.
- Consult a Cybersecurity Expert: Get professional help to investigate the attack and strengthen your system.
If you need strong cybersecurity, Bantech Cyber has you covered. We offer 24/7 monitoring, real-time threat detection, and proactive protection to keep your business safe.
Our experts provide tailored solutions, compliance management, and training for your team. From incident response to vulnerability fixes, we handle everything to protect your future with our Managed Cyber Security Services!
Wrapping Up
So, coming to this point, we can assume that you now have a pretty good idea of how to prevent Man-in-the-Middle attacks. Man-in-the-middle attacks sound scary, but you can protect yourself with a few simple steps. Avoid public Wi-Fi, check for HTTPS, enable 2FA, and stay alert.
Remember, it’s always better to prevent an attack than to fix the damage later. Stay safe online, and if something feels suspicious, trust your instincts.
What steps will you take today to protect yourself from MITM attacks?
