Imagine you buy a product from a trusted brand, but it turns out to be infected with malware. Or your company uses a software update, and suddenly, hackers break into your system.
This is how supply chain attacks happen. Hackers don’t always attack a company directly. They target third-party vendors, software providers, or suppliers to sneak in.
These attacks are increasing. They can cause data leaks, financial loss, and reputation damage. But don’t worry! You can take quick action to stop them.
In this blog, we will explain what these attacks are, how they happen, and how you can prevent supply chain attacks super fast.
Key Takeaways:
|
What is a Supply Chain Attack?
A supply chain attack happens when hackers enter a system by targeting a weak link in the supply chain. Instead of hacking a company directly, they infect software, hardware, or third-party vendors before it even reaches the company.
Why Are Supply Chain Attacks Dangerous?

Supply chain attacks are scary because hackers can steal sensitive data like customer details, passwords, and financial records. They can spread malware to thousands of businesses at once.
Ultimately, these attacks can shut down entire systems, causing huge losses. Businesses can lose their reputation and customer trust, too.
How Fast Are These Attacks Growing?
Supply chain attacks have doubled in the last few years. Let’s look at some recent examples:
| Year | Attack Name | Affected Company | Impact |
| 2023 | MOVEit Attack | Multiple firms | Millions of data records stolen |
| 2023 | 3CX Supply Chain Attack | 3CX Software | Malware infection spread to users |
| 2024 | Okta Cyber Attack | Okta Customers | Unauthorized access to customer accounts |
These attacks can affect any industry—banks, hospitals, tech companies, or even small businesses.
How Do Hackers Exploit the Supply Chain?
Hackers look for weak spots to break in. They find loopholes in:
A. Software Supply Chain Attacks
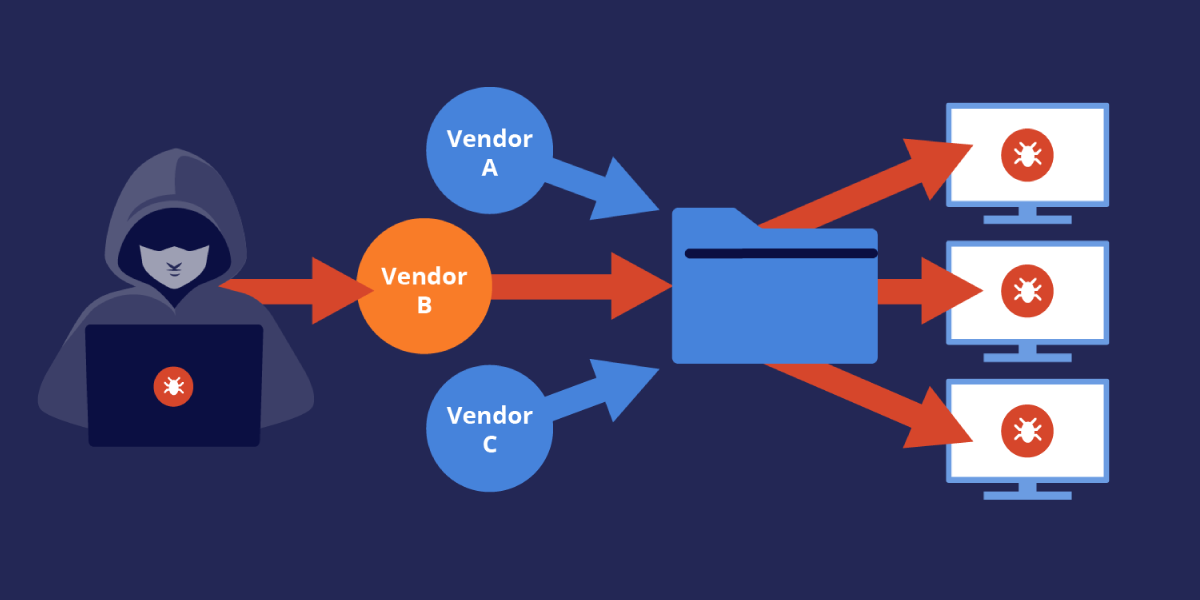
Hackers use software updates to spread malware. They sneak harmful code into a trusted update. When businesses or users install the update, the malware enters their systems. This gives hackers control over sensitive data, networks, and devices.
One of the biggest examples is the SolarWinds Attack (2020). Hackers added malicious code to SolarWinds’ software updates. Thousands of companies, including government agencies, unknowingly installed the infected update. This gave hackers access to sensitive data for months before it was discovered.
To prevent this, always verify software updates, use code integrity checks, and monitor for unusual activity in your systems.
B. Hardware-Based Attacks
Hackers can also attack physical hardware before it reaches a company. They modify components like chips or circuits. These small changes give hackers a chance to spy on or control systems remotely.
For example, some attackers planted spy chips inside servers used by major tech companies. These chips secretly sent data back to hackers. This kind of attack is hard to detect because the hardware looks normal.
To stay safe, buy hardware only from trusted sources. Inspect devices for tampering. Use secure supply chains and monitor all incoming hardware before use.
C. Third-Party Service Attacks

Many businesses use outside companies for IT services, cloud storage, and supply chain management. If these third-party vendors have weak security, hackers can break into their systems. Once inside, they can access sensitive business data, steal customer information, or disrupt operations.
For example, a hacker might target a cloud storage provider that holds your company’s files. If the provider gets hacked, your data is at risk, too.
To reduce this risk, carefully choose vendors who follow strong security practices. Give regular security audits and limit third-party access to only necessary data. Always have a backup plan in case a vendor is compromised.
Common Weak Points in the Supply Chain
| Weak Point | Why It’s a Problem? |
| Outdated Software | No security patches = easy target for hackers |
| Unverified Vendors | No security checks = high risk of breach |
| Weak Passwords | Hackers can easily guess or steal them |
| No Network Monitoring | Attacks go undetected for months |
If these security holes remain open, cyber supply chain attacks can happen anytime.
Steps on How to Prevent Supply Chain Attacks Fast
You can protect yourself! Follow these steps to block supply chain attacks before they happen.
A. Strengthening Vendor & Third-Party Security

Your company works with many suppliers, software providers, and service vendors. Make sure they follow strong security rules.
✔ Check supplier security before working with them.
✔ Demand security compliance from all vendors.
✔ Conduct regular security audits on third-party services.
✔ Only work with verified and trusted suppliers.
🚫 Never trust vendors without checking their security first.
🚫 Avoid working with companies that don’t update their security systems.
B. Enhancing Software & Hardware Security

Software and hardware must be safe before you use them.
✔ Use a Software Bill of Materials (SBOM)—this tracks all software components and ensures they are safe.
✔ Always check code integrity before installing software updates.
✔ Regularly update and patch software to close security gaps.
✔ Buy hardware from trusted sources only—don’t risk using unknown suppliers.
🚫 Never use outdated software—hackers love old systems with weak security.
🚫 Don’t download updates from unknown sources—they may contain malware.
C. Strengthening Network & Data Security

Your company’s network and data need strong protection.
✔ Implement Zero-Trust Security—never assume anyone is safe.
✔ Install Endpoint Detection & Response (EDR) tools—these monitor for suspicious activity.
✔ Set up real-time network monitoring—detect threats before they spread.
🚫 Never ignore security alerts—they can warn you before a breach happens.
🚫 Don’t give excessive access to employees or vendors. Only provide what’s necessary.
D. Employee Training & Awareness

Many cyber-attacks happen because employees make mistakes. Training your staff can prevent supply chain attacks.
✔ Teach employees to spot phishing emails and fake websites.
✔ Limit who can access sensitive supply chain data.
✔ Use Multi-Factor Authentication (MFA)—this adds an extra security layer.
🚫 Don’t assume employees already know how to handle cyber threats.
🚫 Never use weak passwords—always use strong, unique ones.
At Bantech Cyber, we keep your business safe from cyber threats. Our Managed Cyber Security Services work 24/7 to watch over your systems, spot dangers quickly, and stop attacks before they happen.
We protect your data and systems from risks like supply chain attacks and other cyber dangers.
Future of Supply Chain Security
Cyber threats are growing fast. Companies must stay ahead by:
- Using AI-based threat detection for faster responses.
- Adopting blockchain technology to verify and track supply chains.
- Strengthening cybersecurity rules for vendors and suppliers.
Cybersecurity Ventures predicts that the global annual cost of software supply chain attacks on businesses will reach $60 billion by 2025, up from $46 billion in 2023. So, businesses must act now to stay safe.
Check out these blogs for simple guides on preventing Malware Attacks, XSS Attacks, SQL Injection, and Zero-Day Exploits!
Wrapping Up
So, coming to this point, we can assume that you now know how to prevent supply chain attacks fast. Supply chain attacks are increasing, but you can prevent them with the right steps.
Strengthen vendor security, update software, monitor networks, and train employees to reduce risks.
Don’t wait for an attack! Stay alert, stay secure, and protect your supply chain today.
Additionally, explore these helpful blogs to learn how to prevent ransomware, insider threats, cyberattacks, Man-in-the-Middle Attacks, and DDoS attacks!
